Snort + Base en OpenBSD
 Snort es uno de los sistemas de detección de intrusos (IDS) más populares. Base es una de sus múltiples herramientas de análisis básico y OpenBSD es uno de los sistemas operativos más seguros. Haremos una instalación básica para guardar todas las alertas en base de datos (MySQL) y veremos los primeros resultados.
Snort es uno de los sistemas de detección de intrusos (IDS) más populares. Base es una de sus múltiples herramientas de análisis básico y OpenBSD es uno de los sistemas operativos más seguros. Haremos una instalación básica para guardar todas las alertas en base de datos (MySQL) y veremos los primeros resultados.
Antes de nada un poco de teoría de Sistemas de detección de intrusos, tipos y características...
IDS, HIDS
Los IDS, en principio, solo capturan alertas ocurridas en el host local donde están instalados. Aunque, por extensión, todos los Sistemas de Intrusion, del tipo que sean, son tambien llamados IDS:- IDS: Intrusion Detection System
- HIDS: Host Intrusion Detection System
- NIDS: Network Intrusion Detection System
Instalación de Snort
Usaremos binarios puesto que la máquina es bastante obsoleta y no queremos sufrir un infierno compilando. Como podeis comprobar, se trata de una OpenBSD-3.9:# pkg_add -r ftp://ftp.openbsd.org/pub/OpenBSD/3.9/packages/i386/snort-2.4.3-mysql.tgz
snort-2.4.3-mysql:pcre-6.4p1: complete
snort-2.4.3-mysql: complete
--- snort-2.4.3-mysql -------------------
An up-to-date set of rules is needed for Snort to be useful as an IDS.
These can be downloaded manually or net/oinkmaster can be used to
download the latest rules from several different sources.
It is recommended that snort be run as an unprivileged chrooted user.
An _snort user/group and log directory has been created for this
purpose. You should start snort with the following options to take
advantage of this:
-u _snort -g _snort -t /var/snort
and if you want to log:
-l /var/snort/log
#
# wget -c http://www.snort.org/pub-bin/downloads.cgi/Download/vrt_pr/snortrules-pr-2.4.tar.gz
# mkdir -p /etc/snort/rules
# mv snortrules-pr-2.4.tar.gz /etc/snort/rules/
# tar xfvvz snortrules-pr-2.4.tar.gz
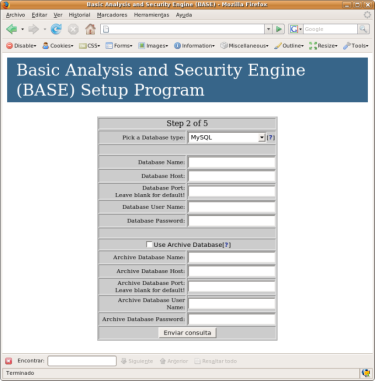
Configuración MySQL
Conectamos con mysql para crear base de datos, usuario y demás (ojo con el socket si lo tenemos configurado para httpd chrooted):# mysql -u root --socket=/var/www/var/run/mysql/mysql.sock -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 7 to server version: 5.0.22
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql> CREATE DATABASE snort;
Query OK, 1 row affected (0.29 sec)
mysql> GRANT INSERT, SELECT ON snort.* to snort@localhost;
Query OK, 0 rows affected (0.53 sec)
mysql> SET PASSWORD FOR snort@localhost = PASSWORD('password');
Query OK, 0 rows affected (0.05 sec)
mysql> GRANT CREATE, UPDATE, INSERT, DELETE, SELECT ON snort.* TO snort@localhost;
Query OK, 0 rows affected (0.00 sec)
# gunzip -d create_mysql.gz
# mysql -u root --socket=/var/www/var/run/mysql/mysql.sock -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 7 to server version: 5.0.22
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql> USE snort;
Database changed
mysql> source create_mysql;
Query OK, 0 rows affected (0.27 sec)
Query OK, 1 row affected (0.11 sec)
Query OK, 0 rows affected (0.04 sec)
Query OK, 0 rows affected (0.02 sec)
Query OK, 0 rows affected (0.00 sec)
...
mysql>
Configuración Snort
En OpenBSD el fichero de configuración principal de Snort se encuentra en /etc/snort/snort.conf, donde tendremos que indicarle al menos que guarde las alertas y los logs en MySQL, parámetros de red y poco más:var HOME_NET 192.168.0.0/24
var DNS_SERVERS $HOME_NET
var SMTP_SERVERS $HOME_NET
var HTTP_SERVERS $HOME_NET
var SQL_SERVERS $HOME_NET
var TELNET_SERVERS $HOME_NET
var SNMP_SERVERS $HOME_NET
var RULE_PATH ../rules/rules
output database: log, mysql, user=snort password=password dbname=snort host=localhost
output database: alert, mysql, user=snort password=password dbname=snort host=localhost
Arrancando Snort
Recomiendan:# snort -bDI -A fast -c /etc/snort/snort.conf
- -b > Log paquetes en formato binario ( tcpdump -r file)
- -D > Modo daemon
- -I > Indica la interfaz por la que llego el paquete
- -A > Tipo de alerta ( fast= una linea en el fichero alert)
- -c > Fichero de reglas
# snort -bDI -A fast -c /etc/snort/snort.conf
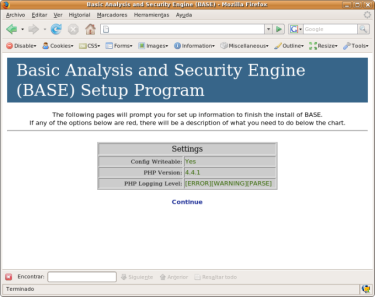
Instalando BASE
Basic Analysis and Security Engine. Desgargamos la última release (19.04.07) dentro del DocumentRoot y descomprimimos:# wget -c http://kent.dl.sourceforge.net/sourceforge/secureideas/base-1.3.5.tar.gz
# tar xvvz base-1.3.5.tar.gz
# cat sql/create_base_tbls_mysql.sql | mysql -u root --socket=/var/www/var/run/mysql/mysql.sock -D snort -p
# mysql -u root --socket=/var/www/var/run/mysql/mysql.sock -p
...
mysql> show tables;
+------------------+
| Tables_in_snort |
+------------------+
| acid_ag |
| acid_ag_alert |
| acid_event |
| acid_ip_cache |
| base_roles |
| base_users |
| data |
| detail |
| encoding |
| event |
| icmphdr |
| iphdr |
| opt |
| reference |
| reference_system |
| schema |
| sensor |
| sig_class |
| sig_reference |
| signature |
| tcphdr |
| udphdr |
+------------------+
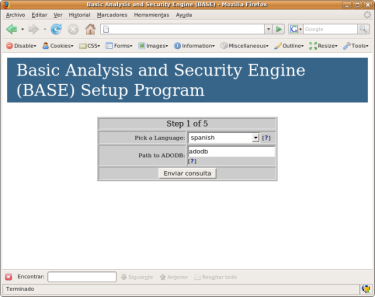
En las instrucciones hay que resolver algunas dependencias de BASE para que funcione correctamente, ADODB es una de ellas:
# wget -c http://puzzle.dl.sourceforge.net/sourceforge/adodb/adodb494.tgz
# tar xfvvz adodb494.tgz
# wget -c http://download.pear.php.net/package/Image_Graph-0.7.2.tgz
# wget -c http://pear.php.net/get/Image_Canvas-0.3.0.tgz
# wget http://pear.php.net/get/Image_Color-1.0.2.tgz
base/
|- Images/
|- Canvas/
|- Graph/
|- docs/
|- tests/
|- Canvas.php
|- Color.php
|- Graph.php
Referencias
- HOWTO_Use_Snort,_Acid,_and_MySQL (gentoo wiki)
- http://www.linuca.org/body.phtml?nIdNoticia=13
- http://www.securityfocus.com/infocus/1640
- http://www.benavent.org/recetas/articles/obsdinstall.php